Getting Started
Spothreat
Spothreat is open source software for leveraging insights from flow and packet analysis. It helps enterprises and service providers gain insight on their network environments through transparency of service delivery and identification of potential security threats or attacks happening among resources operating at cloud scale. While current threat intelligence tools help, identifying unknown threats and attacks remains a challenge. Spothreat provides tools to accelerate companies’ ability to expose suspicious connections and previously unseen attacks using flow and packet analysis technologies.
Spothreat is a solution built to leverage strong technology in both "big data" and scientific computing disciplines. While the solution solves problems end-to-end, components may be leveraged individually or integrated into other solutions. All components can output data in CSV format, maximizing interoperability.
Overview
With the arrival of big data platforms, security organizations can now make data-driven decisions about how they protect their assets. Records of network traffic, captured as network flows, are often stored and analyzed for use in network management. An organization can use this same information to gain insight into what channels corporate information flows through.
By taking into account additional context such as prevalent attacks and key protocols to the organization, the security team can develop a strategy that applies the right amount of per-channel risk mitigation based on the value of the data flowing through it. For an organization, we call this "the port perspective".
There are two vectors that all organizations should evaluate:
- A "wide enough, deep enough" protection strategy that involves both edge prevention and sophisticated detection of unusual behavior
- A deep inspection of key protocols using methods that can scale to the volume of data flowing across that channel
While inspecting specific, unique flows of data that may be important for individual organizations, all organizations can realize significant risk reduction from analysis of network flows and DNS (domain name service) replies.
Spothreat by leveraging strong technology in both Big Data and Scientific Computing disciplines is a solution intended to support this strategy by focusing on “hard security problems” detecting events such as lateral movement, side-channel data escapes, insider issues, or stealthy behavior in general.
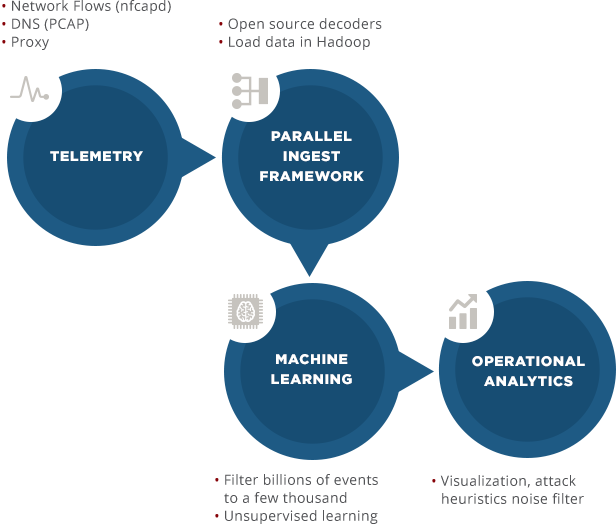
Telemetry
- Flows.
- DNS (pcaps).
- Proxy.
Parallel Ingest Framework
- Open source decoders.
- Load data in Hadoop.
- Data transformation.
Machine Learning
- Filter billion of events to a few thousands.
- Unsupervised learning.
Operational Analytics
- Visualization.
- Attack heuristics.
- Noise filter.

